Scaling VMS
for operational complexity
Role
Product Designer
Team
PO, PM, Developers, UX Researcher, QA
Domain
Security, VMS, B2B SaaS
Key roles
Background Check Officer, Security Manager, Gate Guard
Context
We were building a modern Visitor Management System integrated with access control, security systems, and internal administrative tools. The initial MVP supported personal visits, while all other visitor flows were still handled through emails, spreadsheets, and phone calls.
As the product evolved, we moved to the next phase: expanding the system to support the full operational complexity.
Problem
Stakeholder interviews revealed that security personnel needed to manage contractors, subcontractors, internal employees and the more complex workflows tied to each group. With the introduction of commercial visitors, the existing flows broke.
My goal was to redesign the core visitor experience to support scalable, role-specific workflows.
Research
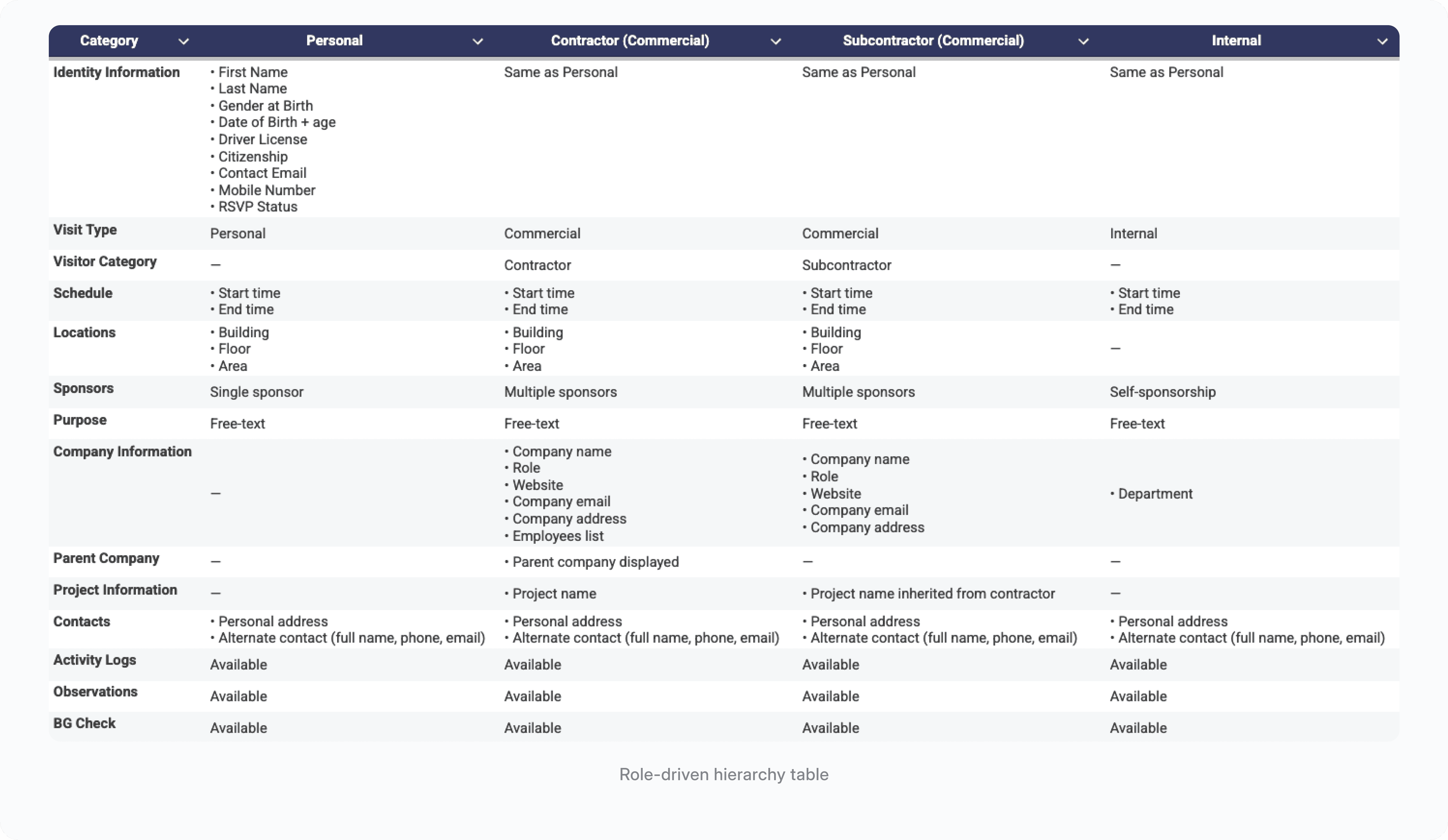
To clarify how different visitor types should be structured, I created a role-driven hierarchy table that aligned design, engineering, and security teams on a shared understanding of the data model.
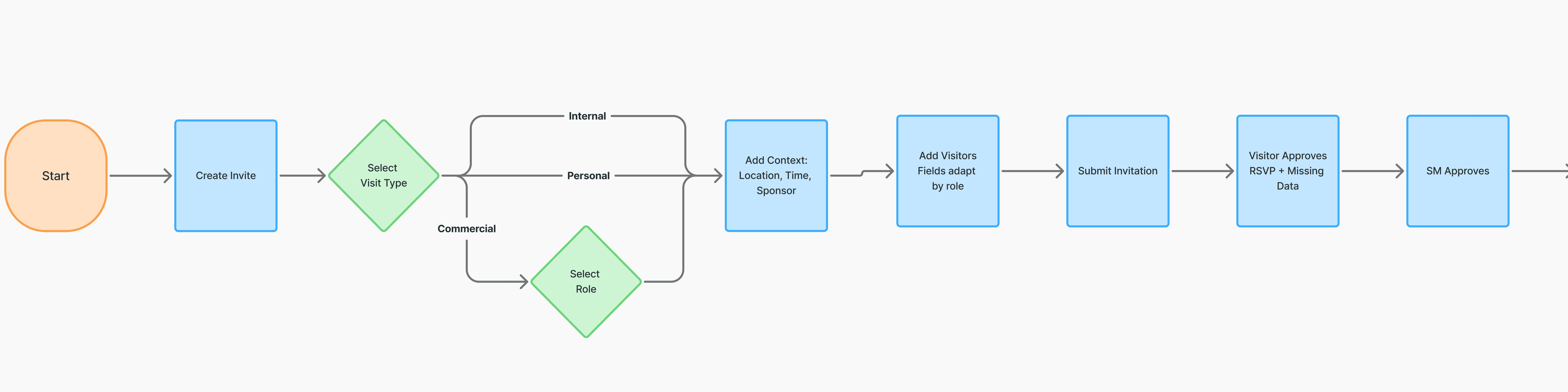
Later, I mapped the end-to-end happy path across Sponsor, Security Manager, BCO and Gate Guard workflows. This revealed how information moves through the system and where role-specific data is required for accurate decision-making.
Design Solutions
The invitation flow starts in the Visitors Dashboard, where a Security Manager creates a new visit.
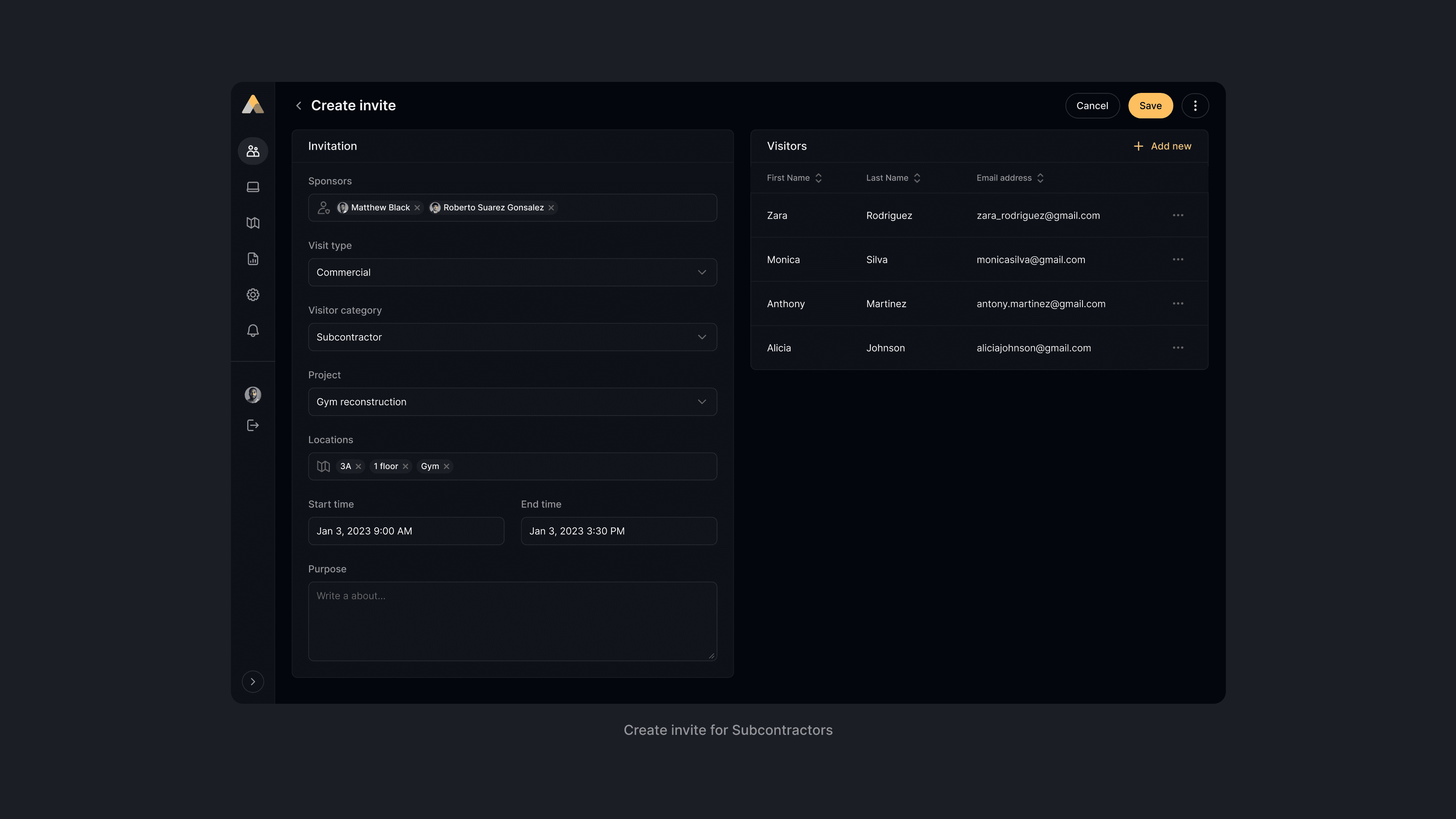
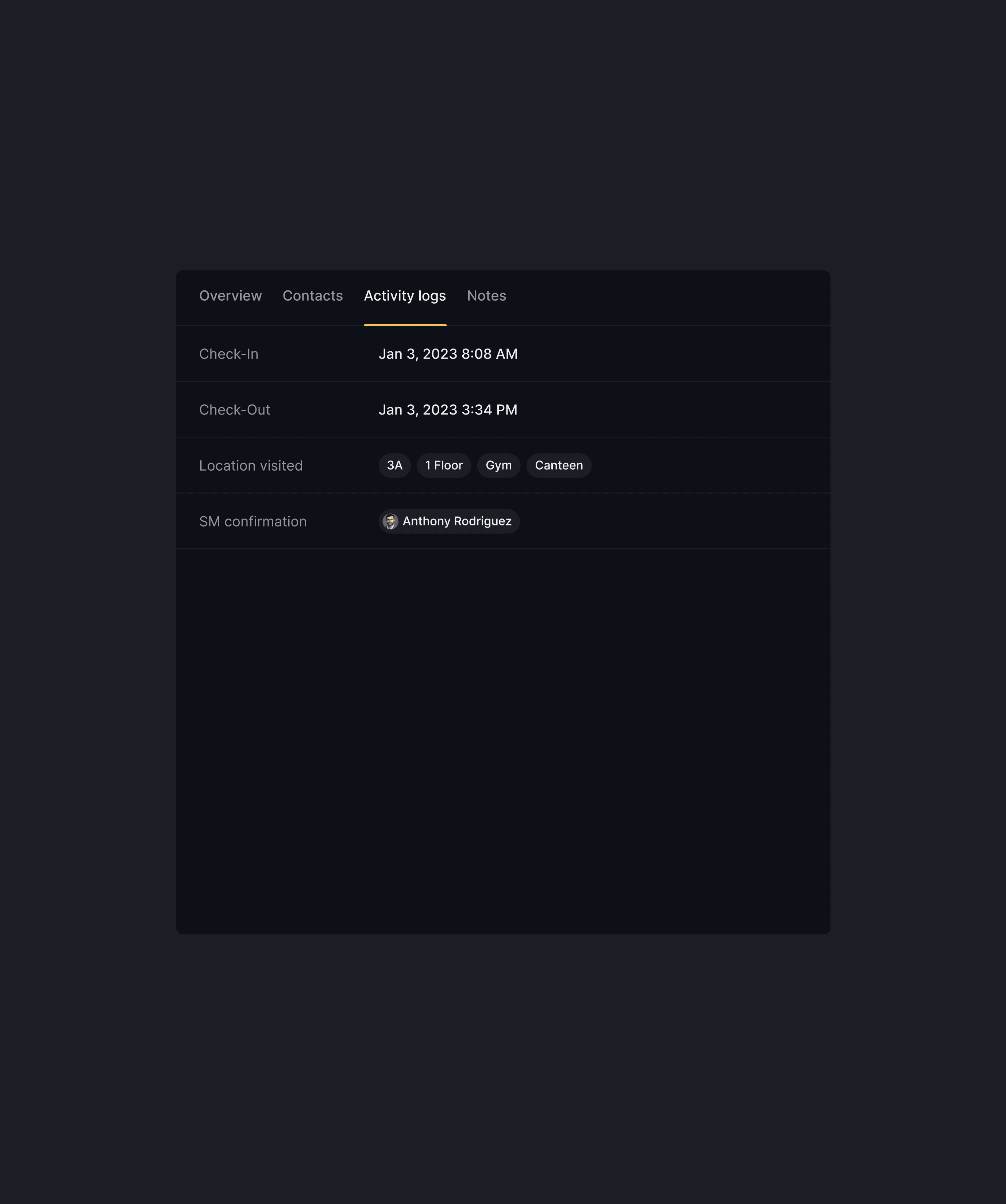
The screens below illustrate how Visitor Details adapt across different system statuses, each with context-appropriate actions for Security Manager.
The main difference between visitor types are:
Personal visitors require only a simple identity overview,
Contractors and Subcontractors display additional metadata including company information, project assignments, and parent-company relationships.
Results
We scaled the VMS from a simple visitor list to a role-aware operational platform. Six months after rollout, we noticed significant improvements in both security performance and operational efficiency:
Gate check-in time decreased from 3.5 minutes to 1 minute, reducing queueing, freeing security personnel, and improving the overall visitor experience.
Security blind spots were removed through through the introduction of structured data, standardized visitor types, and
a complete digital audit trail.The platform passed a full security audit on the first attempt, meeting industry and facility compliance standards.
The system scaled from one facility to three, with no additional redesign.